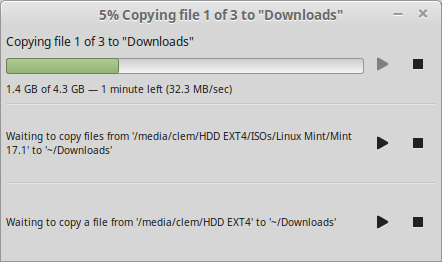
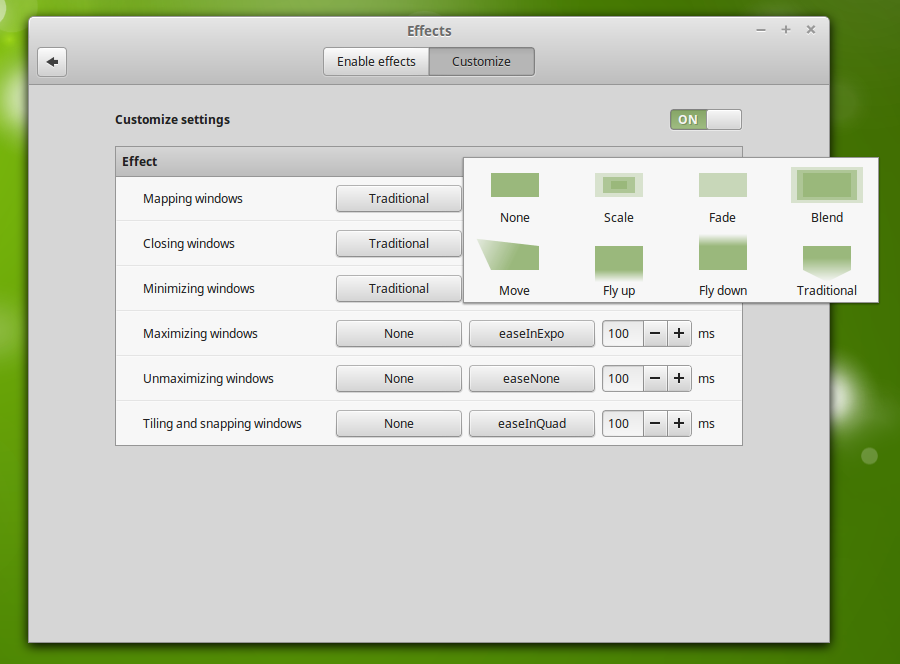
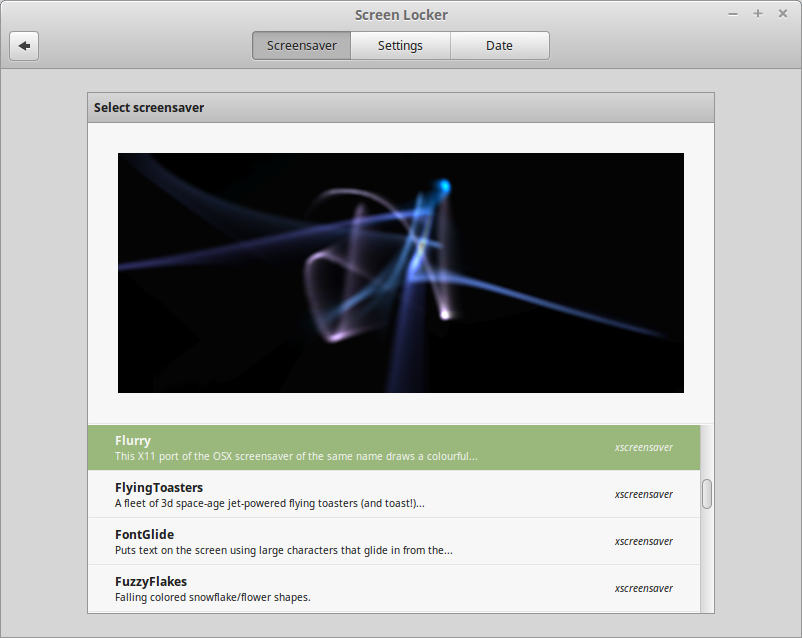
 Source: Cinnamon 2.6 ← Segfault
Source: Cinnamon 2.6 ← Segfault





 Source: Cinnamon 2.6 ← Segfault
Source: Cinnamon 2.6 ← Segfault
I have a confession to make as an internet writer: I block ads. It’s not a habit I formed recently – I have pretty much blocked ads my entire life, in every medium that I can. In middle…
Source: Adblocking And The End Of Big Advertising | TechCrunch
Thunderbolt 3 integrates USB 3.1, optional 100W power delivery, 5K @ 60Hz display.
Source: Thunderbolt 3 embraces USB Type-C connector, doubles bandwidth to 40Gbps | Ars Technica
“Rep Guidance” software helps Verizon convince you not to cancel.
Source: Verizon FiOS reps know what TV channels you watch | Ars Technica
We’ve all, at some stage, found ourselves in the scenario where we pass our phones over to a friend, with the intent on showing them a photo or video, and they take it upon themselves to scan through the entire library. Many of us harbor snaps that we’d probably not want to share with everybody, and so when this unsolicited scanning frenzy begins, we often lean over to retrieve our devices before the worst occurs. But there is an easier way. There just so happens to be an in-built iOS feature that allows you to completely disable and enable touch browsing in a swift, convenient manner.
Source: This iOS Trick Prevents People From Swiping Through Your Photos On iPhone | Redmond Pie
Google has historically been chastised for its lack of transparency and ease of configuration as far as it comes to privacy and security of accounts, which is why at this week’s Google I/O the company announced My Account, a new Web page that aims to put all of Google’s account-based ills right.
Source: New ‘My Account’ Hub Tells You Everything Google Knows About You | Redmond Pie
In addition to launching the GeForce GTX 980 Ti today, NVIDIA also made a number of other disclosures related to its variable refresh rate G-SYNC display and VR technologies. Along with getting windowed-mode support, desktop G-SYNC is also getting a few more display offerings courtesy of Acer and Asus, with […]
Sour
 ce: Gaming Notebook Displays Are About To Get A Major Upgrade – Forbes
ce: Gaming Notebook Displays Are About To Get A Major Upgrade – Forbes