Source: MScholtes/PS2EXE: Module to compile powershell scripts to executables
Category Archives: sysadmin
Ventoy
Ventoy is an open source tool to create bootable USB drive for ISO/WIM/IMG/VHD(x)/EFI files.
With ventoy, you don’t need to format the disk over and over, you just need to copy the ISO/WIM/IMG/VHD(x)/EFI files to the USB drive and boot them directly.
You can copy many files at a time and ventoy will give you a boot menu to select them (screenshot).
You can also browse ISO/WIM/IMG/VHD(x)/EFI files in local disks and boot them.
x86 Legacy BIOS, IA32 UEFI, x86_64 UEFI, ARM64 UEFI and MIPS64EL UEFI are supported in the same way.
Most types of OS supported (Windows/WinPE/Linux/ChromeOS/Unix/VMware/Xen…)
Source: Ventoy
Home · huginn/huginn Wiki
Source: Home · huginn/huginn Wiki
teamviewer/TeamViewerPS: TeamViewerPS allows to interact with the TeamViewer Web API as well as a locally installed TeamViewer client.
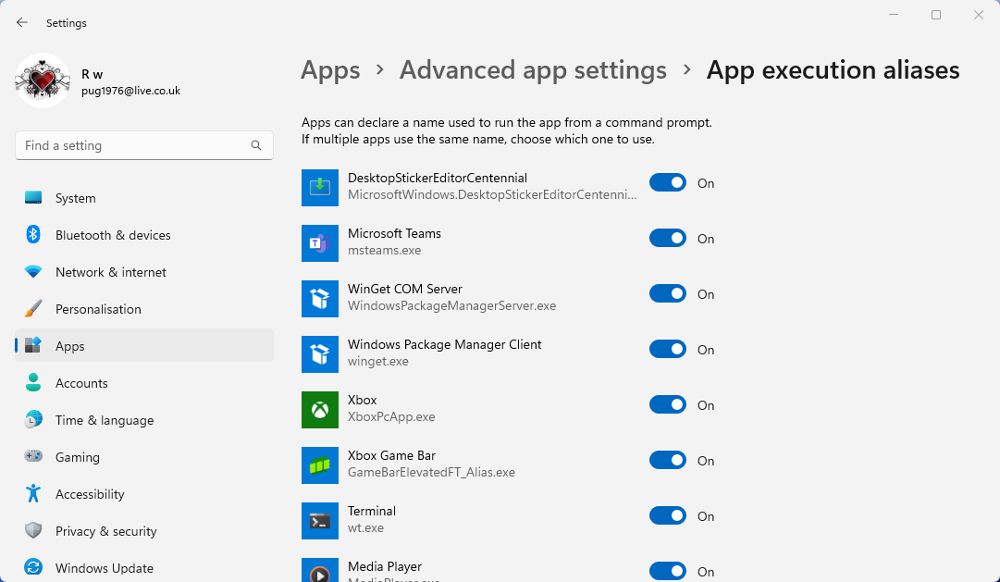
What Are App Execution Aliases, and How Do You Use Them?
What Are App Execution Aliases, and How Do You Use Them?
If you’re trying to open an app like Microsoft Paint in the Run Dialog and see an error message, it could be caused by your app aliases. But what exactly are App Execution Aliases, where do you find them, and how do you use them?
What Are App Execution Aliases?
An alias is an alternative name given to something. The most obvious example is the codename given to a spy or undercover agent. On Windows, aliases have nothing to do with spying. Instead, they are used for streamlining tasks, such as entering commands.
Windows 10 and 11 both allow aliases to be declared for some apps by default. The available apps vary but are often those commonly associated with command line tools. Giving an app an alias allows it to be executed using a shorter title rather than the full name or path.
App aliases can be used in several Windows Command Line Interfaces (CLI), including the Run Dialog, Command Prompt, and PowerShell. If you use these tools with any regularity, app aliases can help to streamline entering commands.
How to Enable App Execution Aliases in Settings
You can enable and disable aliases for compatible apps in the main settings in both Windows 10 and 11. If more than one app uses the same alias name, you can choose which has the alias applied to it.
In Windows 11:
- Open Settings > Apps, and look for Advanced app settings.
- In the advanced app settings, click App execution aliases to see the list of compatible apps.
- Use the slider switches to enable or disable the alias for each app. You can see the alias name below each app.
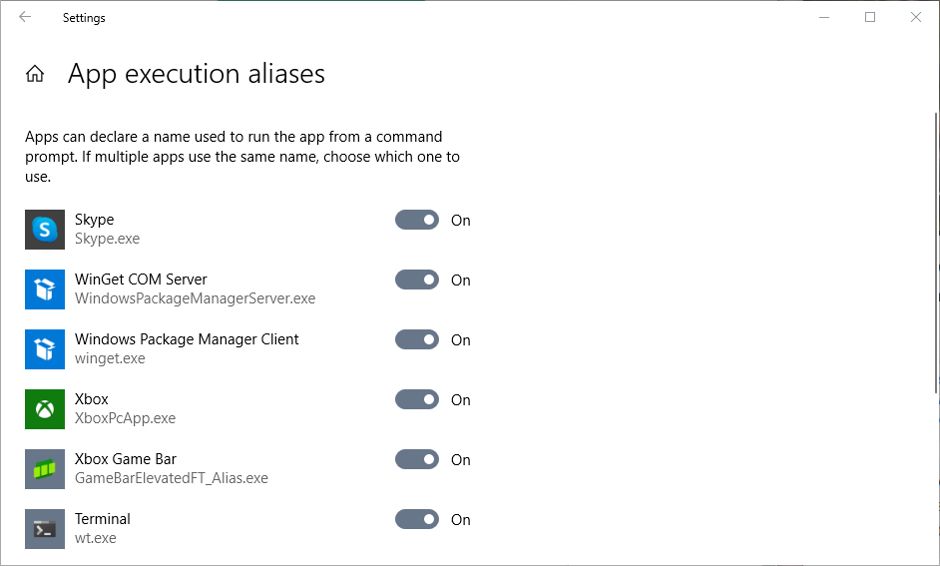
In Windows 10:
- If you’re using Windows 10, you’ll find the aliases in Settings > Apps & features.
- Click the App execution aliases link near the top of the Apps & features page.
- You can then enable and disable aliases using the switches.
By default, in both Windows 10 and 11, you can only enable or disable existing app aliases. But if you don’t mind editing the Registry, you can create new aliases for many other apps.
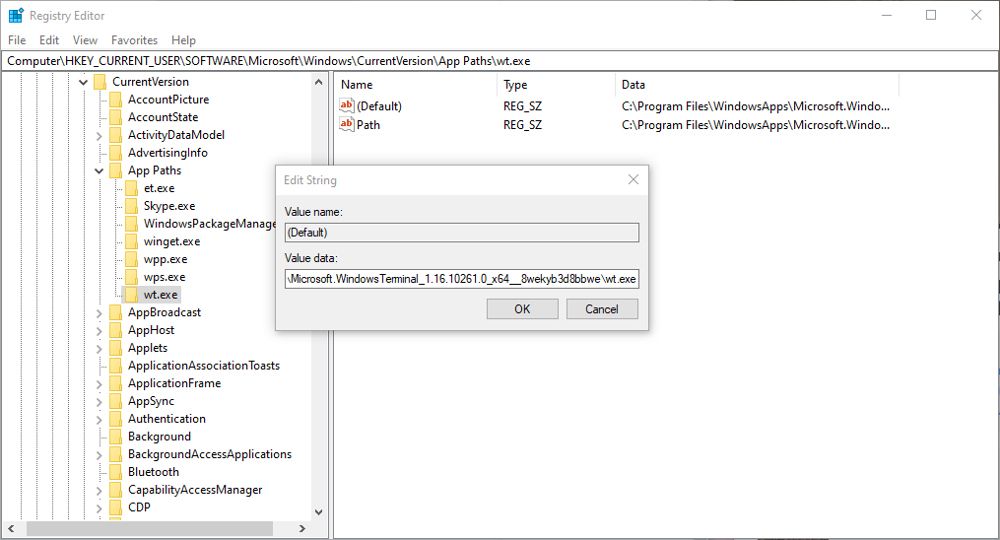
Create App Execution Aliases in Registry Editor
Before editing or creating registry keys, it is advisable to create a full backup of the Windows Registry. Of course, you should also ensure you understand how to restore the Registry from that backup.
The process below for creating app execution aliases in the Registry Editor should be the same in both Windows 10 and 11.
- Open Windows Search, type Registry Editor, and click on the search result to open it.
- In the editor, navigate to HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\App Paths.
- Next, right-click on the App Paths key in the left-hand pane, and select New > Key.
- Give the new key an alias name that relates to the app and ends with .exe. For example, if the alias is for Calendar, call it something like cal.exe.
- With the alias selected, double-click the Default value in the right-hand pane.
- In the Value data field, you will need to enter the full path to the app executable file. For example C:\Program Files (x86)\Calendar.exe.
- Right-click in the right pane and select New > String value. Name the string path. The change the Value data to the same path as above, but without the app filename.
You can now close the Registry Editor. The new App Execution Alias will now be available to use in the Windows CLIs.
Using and Creating App Execution Aliases
Entering commands into tools such as Command Prompt and PowerShell can be laborious. You can streamline that process by enabling or creating aliases for apps that commonly feature in those commands. Why type out a full path to an executable file when you can point to it with a few keystrokes?
Source: What Are App Execution Aliases, and How Do You Use Them?
How to ALWAYS show all the Icons in Notification area of Windows
Use Control Panel to show the icons
To always show all the Icons in the System Tray or Notification area of Windows 11/10, via Control Panel follow these steps:
- Press Win+R to open the Run prompt.
- Enter this value:
explorer shell:::{05d7b0f4-2121-4eff-bf6b-ed3f69b894d9}- Tick the Always show all icons and notifications on the taskbar checkbox.
- Click the OK button.
Source: How to ALWAYS show all the Icons in Notification area of Windows
Useful pfSense commands – OneByte | tech blog
Here are some commands that I’ve compiled over my time working with pfSense. My pfSense cheat sheet!
Description Command Reload the Firewall with all the configuration. This also restarts the webgui and sshd – but keeps the current ssh sessions active just as a regular sshd restart. /etc/rc.reload_all Manually edit the configuration in /conf/config.xml. Once file has been saved and editor exited, the /tmp/config.cache is removed so the next config reload event will load config.xml, not the cached version. You could run the next command to trigger an instant reload. viconfig Show rule/filter information pfctl -s rules Show rule/filter info for what FILTER rules hit pfctl -v -s rules Show rule/filter info, includes rule counters, ID numbers, etc. pfctl -vvsr Shows the current state table pfctl -ss Shows current filter rules pfctl -sr Show as much as possible. pfctl -sa Shows current NAT rules pfctl -sn Show NAT information for which rules hit pfctl -v -s nat Show NAT information for interface GE1 pfctl -s nat -i ge1 Show QUEUE information pfctl -s queue Show LABEL information pfctl -s label Show contents of the STATE table pfctl -s state Show statistics for state tables and packet normalization pfctl -s info Show everything pfctl -s all Enable the packet filter – enables all firewall functions pfctl -e Disable the packet filter – disables all firewall functions pfctl -d Run qiuet pfctl -q flush ALL pfctl -F all flush only the RULES pfctl -F rules flush only queues pfctl -f queue flush only NAT pfctl -F nat pfctl -F info flush all stats that are not part of any rule pfctl -z clear all counters Playback Scripts Changes password for the defined user. Prompts to reset the account properties if it is disabled or expired pfSsh.php playback changepassword Enable/Disable CARP high availability functions. Will deactivate the CARP virtual IP addresses. Does not persist across reboots. pfSsh.php playback disablecard
pfSsh.php playback enablecarp
Enable/Disable CARP maintenance mode. This leaves CARP active but demotes the unit so that another can assume control. Maintenance mode will persist across reboots. pfSsh.php playback disablecarpmaint
pfSsh.php playback enablecarpmaint
Removes all DHCP configuration from the firewall causing DHCP to be disabled. It completely removes all of its settings. pfSsh.php playback disabledhcp Disables the HTTP_REFERER check in Browser HTTP_REFERER enforcement. This can aid in gaining access to the GUI if the browser session is triggering this protection. pfSsh.php playback disablereferercheck Adds an allow all rule for IPv4 and IPv6 to the WAN interface Be extremely careful with this option, it is meant to be a temporary measure to gain access to services on the WAN interface of the firewall in situations where the LAN is not usable. Once proper access rules are put in place, remove the rules added by this script.
pfSsh.php playback enableallowallwan Enables the SSH daemon – same as the menu option or in the GUI pfSsh.php playback enablesshd This script looks for a config.xml file on the external device, such as a USB drive. Then move it in place for use by the firewall. pfSsh.php playback externalconfiglocator Prints the current gateway status and statistics. This also accepts an optional parameter brief, which prints only the gateway name and status, omitting the addresses and statistical data. pfSsh.php playback gatewaystatus Creates a new self-signed certificate for the firewall and activates for use in the GUI. This can be useful in cases where the previous certificate is invalid or unusable. It also fills in the certificate details using the firewall hostname and other custom information for better identifying your host. pfSsh.php playback generateguicert A complex script that synchronizes the PHP and other script sources with the files from the pfSense GitHub repository. This is most useful on development snapshots to pick up changes from more recent commits. This script can be dangerous to use in other circumstances. Only use this under the direction of a knowledgeable developer or support representative.
pfSsh.php playback gitsync pfSsh.php playback install pkg pfSsh.php playback listpkg
pfSsh.php playback uninstallpkg
View additional rules in anchors from packages or features, such as UPnP. pfSsh.php playback pfanchordrill Prints the contents of all pf tables, which contain addresses used in firewall aliases, as well as built-in system tables for features such as bogon network blocking, snort, and GUI/SSH lockout. This is also useful for checking if a specific IP address is found in any table, rather than searching individually. pfSsh.php playback pftabledrill Removes all traces of package configuration data from the running config.xml. This can be useful if a package has corrupted settings or has otherwise left the packages in an inconsistent state. pfSsh.php playback removepkgconfig Removes ALTQ traffic shaper settings, which can be useful if the shaper configuration is preventing rules from loading or is otherwise incorrect and preventing proper operations of the firewall. pfSsh.php playback removeshaper Resets the GUI settings for widgets, dashboard columns, the theme, and other GUI-related settings. It can return the GUI, particularly the dashboard, to a stable state if it is not functioning properly. pfSsh.php playback resetwebgui Disables and re-enables each WAN-type interface, which reapplies the interface configuration pfSsh.php playback restartallwan Stops and restarts the DHCP daemon pfSsh.php playback restartdhcpd Rewrites and reloads the IPsec configuration for strongSwan pfSsh.php playback restartipsec Controls the services running on the firewall, similar to interacting with services at Status > Services The action can be stop, start, or restart.
The service name is the name of the services as found under Status > Services. If the name includes a space, enclose the name in quotes.
The service-specific options vary depending on the service, they are used to uniquely identify services with multiple instances, such as OpenVPN or Captive Portal entries.
pfSsh.php playback svc playback svc <action> <service name> [service-specific options]
The shell version of Easy Rule, easyrule, can add a firewall rule from a shell prompt. When the easyrule command is run without parameters, it prints a usage message to explain its syntax. The way easyrule adds a block rule using an alias, or a precise pass rule specifying the protocol, source, and destination, work similar to the GUI version.
easyrule pass/block <interface> <protocol> <source IP> <destination ip> [destination port] easyrule pass wan tcp 0.0.0.0/0 192.168.0.1 80
easyrule pass wan icmp 1.1.1.1 192.168.0.1
easyrule block wan 1.1.1.1
show table addvhosts pfctl -t addvhosts -T show view global information about all tables pfctl -vvsTables add entry to table addvhosts pfctl -t addvhosts -T add 192.168.1.50 add a network to table addvhosts pfctl -t addvhosts -T add 192.168.1.0/16 delete nework from table addvhosts pfctl -t addvhosts -T delete 192.168.1.0/16 remove all entries from table addvhosts pfctl -t addvhosts -T flush delete table addvhosts entirely pfctl -t addvhosts -T kill reload table addvhosts on the fly pfctl -t addvhosts -T replace -f /etc/addvhosts find ip address 192.168.1.40 in table addvhosts pfctl -t addvhosts -T test 192.168.1.40 load a new table definition pfctl -T load -f /etc/pf.conf stats for each ip address in table addvhosts pfctl -t addvhosts -T show -v output reset all counters for table addvhosts pfctl -t addvhosts -T zero Manual restart of openVPN process echo “<?php include(‘openvpn.inc’); openvpn_resync_all();?>” | php -q
How do I change the local user account name in Windows 10?
How do I change the local user account name in Windows 10?
Windows Key+R > Type netplwiz > Enter
In the User Accounts window, on the Users tab, select the user account you wish to change the name for and click Properties.
In the property sheet, on the General tab, edit the User name.Click Apply followed by OK and you’re done
20 Windows Command Prompt (CMD) Commands You Must Know
Windows Command Prompt Commands
If you haven’t poked around inside Windows’ command line, you’re missing out. There are lots of handy tools you can use if you know the correct things to type.
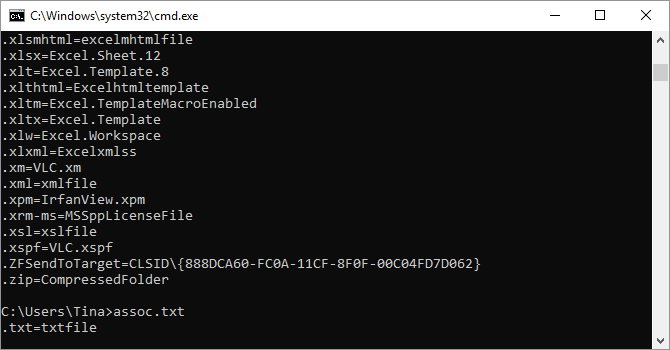
1. Assoc
Most files on Windows are associated with a specific program that is assigned to open the file by default. At times, remembering these associations can become confusing. You can remind yourself by entering the command assoc to display a full list of filename extensions and program associations.
You can also extend the command to change file associations. For example, assoc .txt= will change the file association for text files to whatever program you enter after the equal sign. The assoc command itself will reveal both the extension names and program names, which will help you properly use this command.
In Windows 10, you can view a more user-friendly interface that also lets you change file type associations on the spot. Head to Settings (Windows + I) > Apps > Default apps > Choose default app by file type.
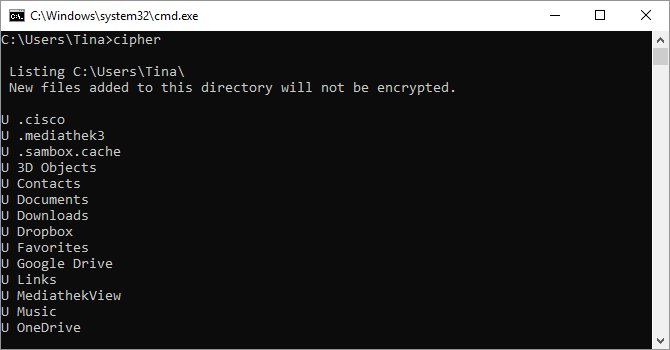
2. Cipher
Deleting files on a mechanical hard drive doesn’t really delete them at all. Instead, it marks the files as no longer accessible and the space they took up as free. The files remain recoverable until the system overwrites them with new data, which can take some time.
The cipher command, however, lets you wipe a directory on an NTFS-formatted volume by writing random data to it. To wipe your C drive, for example, you’d use the cipher /w:d command, which will wipe free space on the drive. The command does not overwrite undeleted data, so you will not wipe out the files you need by running this command.
When you run the cipher command by itself, it returns the encryption state of the current directory and the files it contains. Use cipher /e:<filename> to encrypt a file, cipher /c:<filename> to retrieve information about encrypted files, and cipher /d:<filename> to decrypt the selected file. Most of these commands are redundant with the Windows encryption tool BitLocker.
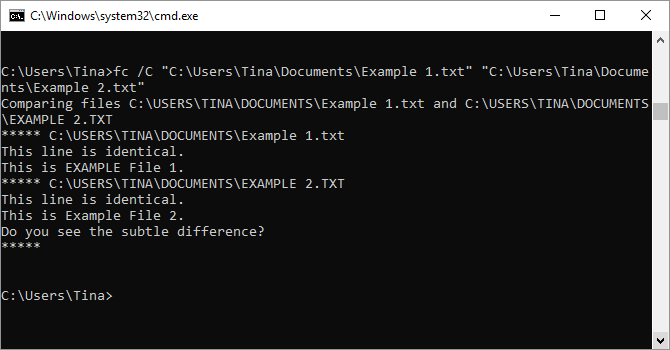
3. File Compare
You can use this command to identify differences in text between two files. It’s particularly useful for writers and programmers trying to find small changes between two versions of a file. Simply type fc and then the directory path and file name of the two files you want to compare.
You can also extend the command in several ways. Typing /b compares only binary output, /c disregards the case of text in the comparison, and /l only compares ASCII text.
So, for example, you could use the following:
fc /l "C:\Program Files (x86)\example1.doc" "C:\Program Files (x86)\example2.doc"The above command compares ASCII text in two Word documents.
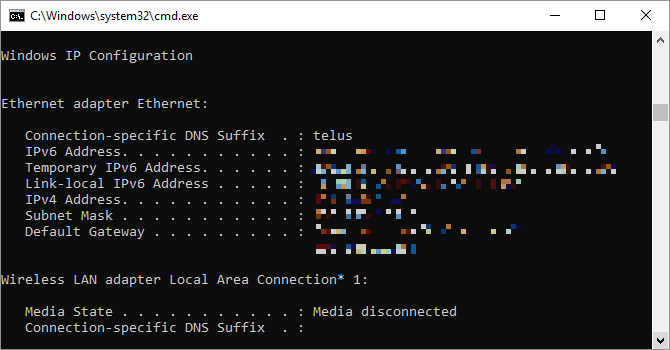
4. Ipconfig
This command relays the IP address that your computer is currently using. However, if you’re behind a router (like most computers today), you’ll instead receive the local network address of the router.
Still, ipconfig is useful because of its extensions. ipconfig /release followed by ipconfig /renew can force your Windows PC into asking for a new IP address, which is useful if your computer claims one isn’t available. You can also use ipconfig /flushdns to refresh your DNS address. These commands are great if the Windows network troubleshooter chokes, which does happen on occasion.
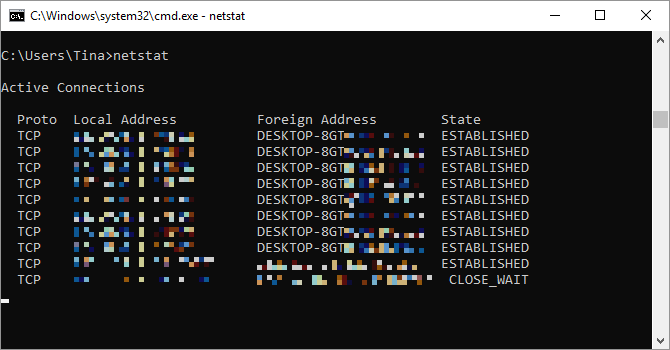
5. Netstat
Entering the command netstat -an will provide you with a list of currently open ports and related IP addresses. This command will also tell you what state the port is in; listening, established, or closed.
This is a great command for when you’re trying to troubleshoot devices connected to your PC or when you fear a Trojan infected your system and you’re trying to locate a malicious connection.
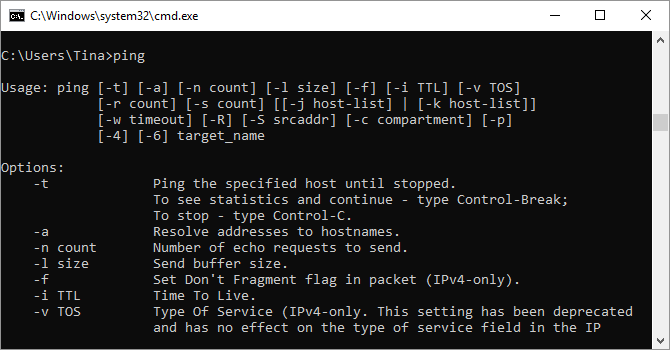
6. Ping
Sometimes, you need to know whether packets are making it to a specific networked device. That’s where ping comes in handy.
Typing ping followed by an IP address or web domain will send a series of test packets to the specified address. If they arrive and are returned, you know the device is capable of communicating with your PC; if it fails, you know that there’s something blocking communication between the device and your computer. This can help you decide if the root of the issue is an improper configuration or a failure of network hardware.
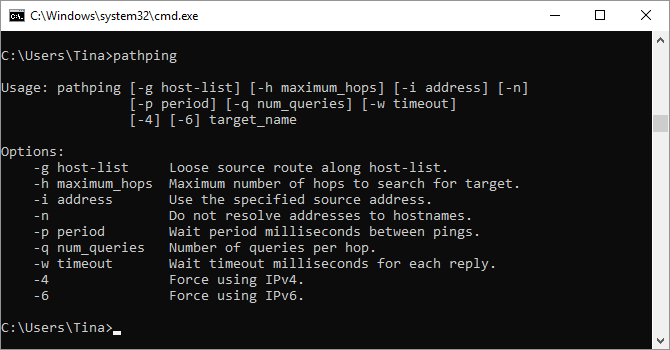
7. PathPing
This is a more advanced version of ping that’s useful if there are multiple routers between your PC and the device you’re testing. Like ping, you use this command by typing pathping followed by the IP address, but unlike ping, pathping also relays some information about the route the test packets take.
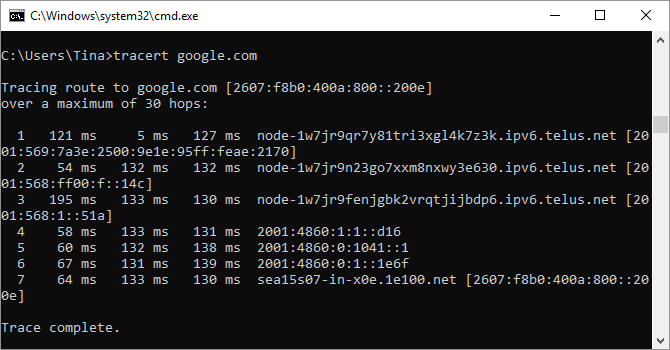
8. Tracert
The tracert command is similar to pathping. Once again, type tracert followed by the IP address or domain you’d like to trace. You’ll receive information about each step in the route between your PC and the target. Unlike pathping, however, tracert also tracks how much time (in milliseconds) each hop between servers or devices takes.
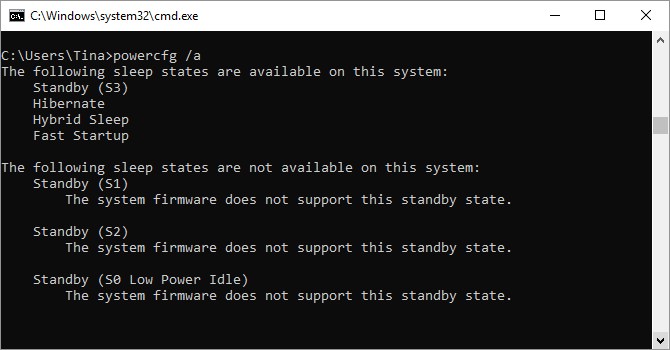
9. Powercfg
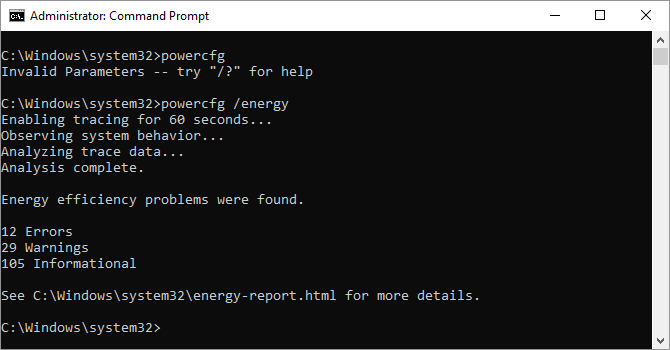
Powercfg is a very powerful command for managing and tracking how your computer uses energy. You can use the command powercfg hibernate on and powercfg hibernate off to manage hibernation, and you can also use the command powercfg /a to view the power-saving states currently available on your PC.
Another useful command is powercfg /devicequery s1_supported, which displays a list of devices on your computer that support connected standby. When enabled, you can use these devices to bring your computer out of standby, even remotely.
You can enable this by selecting the device in Device Manager, opening its properties, going to the Power Management tab, and then checking the Allow this device to wake the computer box.
Powercfg /lastwake will show you what device last woke your PC from a sleep state. You can use this command to troubleshoot your PC if it seems to wake from sleep at random.
You can use the powercfg /energy command to build a detailed power consumption report for your PC. The report saves to the directory indicated after the command finishes.
This report will let you know of any system faults that might increase power consumption, like devices blocking certain sleep modes, or poorly configured to respond to your power management settings.
Windows 8 added powercfg /batteryreport, which provides a detailed analysis of battery use, if applicable. Normally output to your Windows user directory, the report provides details about the time and length of charge and discharge cycles, lifetime average battery life, and estimated battery capacity.
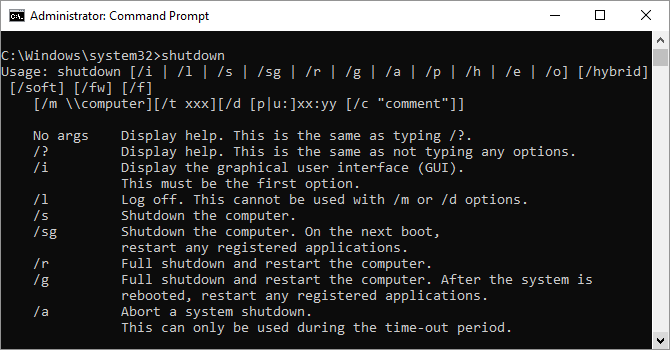
10. Shutdown
Windows 8 introduced the shutdown command that, you guessed it, shuts down your computer.
This is, of course, redundant with the already easily accessed shutdown button, but what’s not redundant is the shutdown /r /o command, which restarts your PC and launches the Advanced Start Options menu, which is where you can access Safe Mode and Windows recovery utilities. This is useful if you want to restart your computer for troubleshooting purposes.
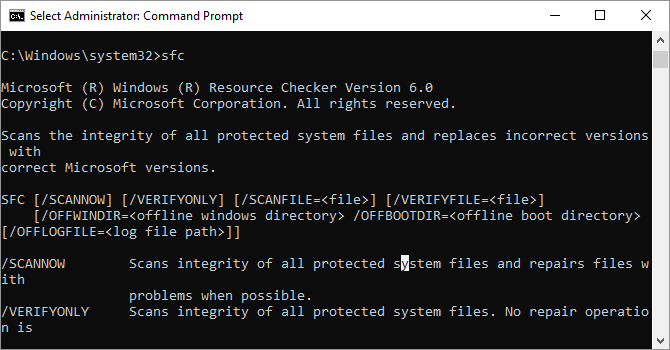
11. System File Checker
System File Checker is an automatic scan and repair tool that focuses on Windows system files.
You will need to run the command prompt with administrator privileges and enter the command sfc /scannow. If SFC finds any corrupt or missing files, it will automatically replace them using cached copies kept by Windows for this purpose alone. The command can require a half-hour to run on older notebooks.
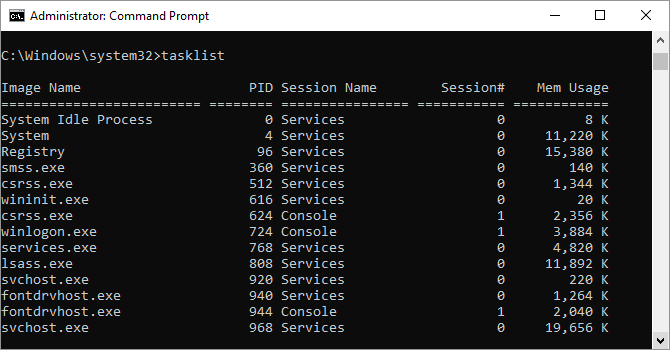
12. Tasklist
You can use the tasklist command to provide a current list of all tasks running on your PC. Though somewhat redundant with Task Manager, the command may sometimes find tasks hidden from view in that utility.
There’s also a wide range of modifiers. Tasklist -svc shows services related to each task, use tasklist -v to obtain more detail on each task, and tasklist -m will locate DLL files associated with active tasks. These commands are useful for advanced troubleshooting.
Our reader Eric noted that you can “get the name of the executable associated with the particular process ID you’re interested in.” The command for that operation is tasklist | find [process id].
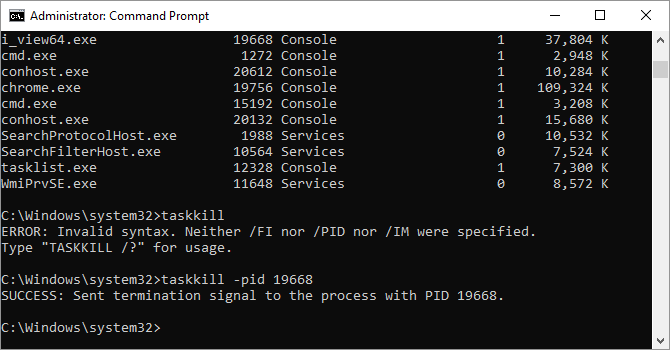
13. Taskkill
Tasks that appear in the tasklist command will have an executable and process ID (a four- or five-digit number) associated with them. You can force stop a program using taskkill -im followed by the executable’s name, or taskkill -pid followed by the process ID. Again, this is a bit redundant with Task Manager, but you can use it to kill otherwise unresponsive or hidden programs.
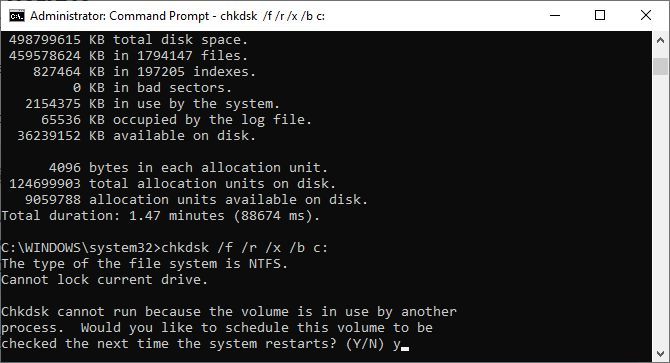
14. Chkdsk
Windows automatically marks your drive for a diagnostic chkdsk scan when symptoms indicate that a local drive has bad sectors, lost clusters, or other logical or physical errors.
If you suspect your hard drive is failing, you can manually initiate a scan. The most basic command is chkdsk c:, which will immediately scan the C: drive, without a need to restart the computer. If you add parameters like /f, /r, /x, or /b, such as in chkdsk /f /r /x /b c:, chkdsk will also fix errors, recover data, dismount the drive, or clear the list of bad sectors, respectively. These actions require a reboot, as they can only run with Windows powered down.
If you see chkdsk run at startup, let it do its thing. If it gets stuck, however, refer to our chkdsk troubleshooting article.
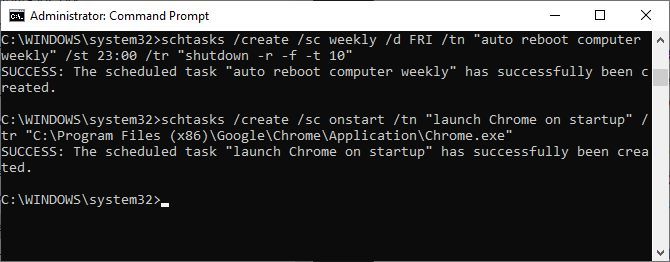
15. schtasks
Schtasks is your command prompt access to the Task Scheduler, one of many underrated Windows administrative tools. While you can use the GUI to manage your scheduled tasks, the command prompt lets you copy&paste complex commands to set up multiple similar tasks without having to click through various options. Ultimately, it’s much easier to use, once you’ve committed key parameters to memory.
For example, you could schedule your computer to reboot at 11pm every Friday:
schtasks /create /sc weekly /d FRI /tn "auto reboot computer weekly" /st 23:00 /tr "shutdown -r -f -t 10"To complement your weekly reboot, you could schedule tasks to launch specific programs on startup:
schtasks /create /sc onstart /tn "launch Chrome on startup" /tr "C:\Program Files (x86)\Google\Chrome\Application\Chrome.exe"To duplicate the above command for different programs, just copy, paste, and modify it as needed.
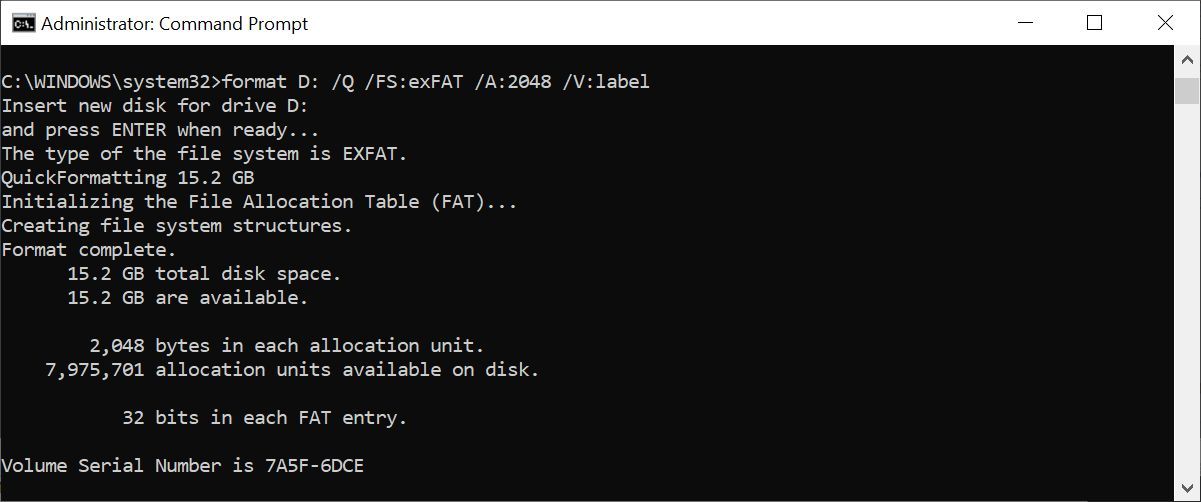
16. Format
When you need to format a drive, you can either use the Windows File Explorer GUI or you can turn to the command prompt. You’ll need Administrator rights to use this command. Be sure you specify the volume you want to format, followed by the desired parameters.
The command below will quick-format the D drive with the exFAT file system, with an allocation unit size of 2048 bytes, and rename the volume to “label” (without the quotes).
format D: /Q /FS:exFAT /A:2048 /V:labelYou can also use this command to dismount a volume (/X) or, if it’s formatted with NTFS, make file compression the default setting (/R). If you’re stuck, use format /? to summon help.
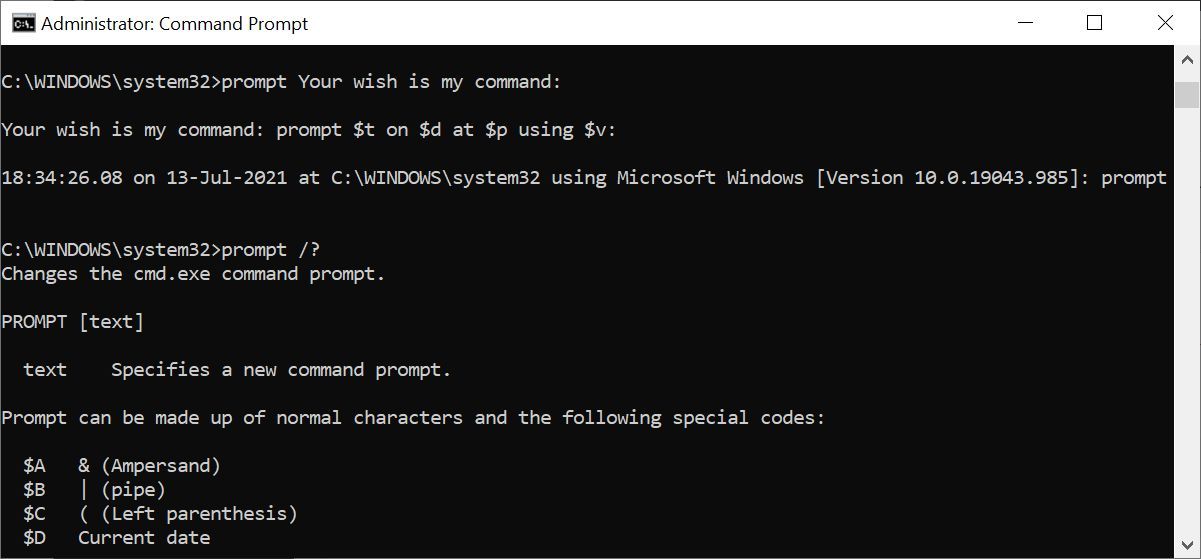
17. prompt
Would you like to customize your command prompt to include instructions or certain information? With the prompt command, you can!
Try this one:
prompt Your wish is my command:You can add the current time, date, drive and path, Windows version number, and so much more.
prompt $t on $d at $p using $v:Type “prompt” to reset your command prompt to default settings or just restart the command prompt. Unfortunately, these settings aren’t permanent.
18. cls
Cluttered up your command prompt window trying out all the commands above? There’s one last command you need to know to clean it all up again.
clsThat’s all. Bet Marie Kondo didn’t know that one.
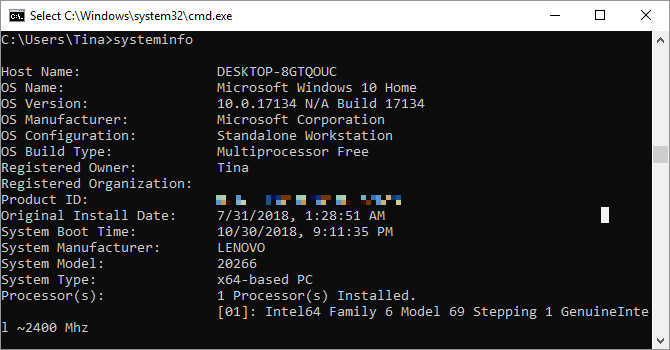
19. Systeminfo
This command will give you a detailed configuration overview of your computer. The list covers your operating system and hardware. For example, you can look up the original Windows installation date, the last boot time, your BIOS version, total and available memory, installed hotfixes, network card configurations, and more.
Use systeminfo /s followed by the hostname of a computer on your local network, to remotely grab the information for that system. This may require additional syntax elements for the domain, user name, and password, like this:
systeminfo /s [host_name] /u [domain]\[user_name] /p [user_password]20. Driverquery
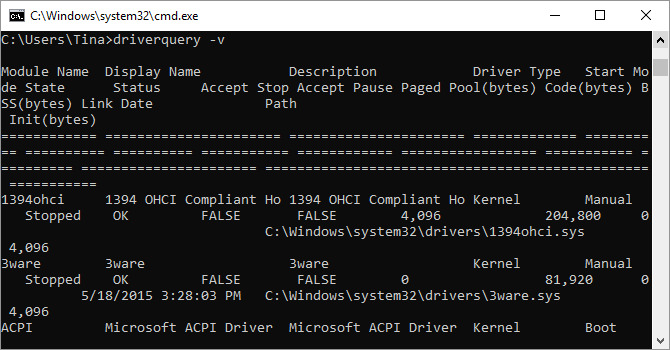
Drivers remain among the most important software installed on a PC. Improperly configured, missing, or old Windows drivers can cause all sorts of trouble, so it’s good to have access to a list of drivers on your PC.
That’s exactly what the driverquery command does. You can extend it to driverquery -v to obtain more information, including the directory in which the driver is installed. Unfortunately, this command isn’t relevant post Windows 8 or Windows Server 2012.
Windows 8 Only: Recovery Image
Virtually all Windows 8/8.1 computers ship from the factory with a recovery image, but the image may include bloatware you’d rather not have re-installed. Once you’ve uninstalled the software you can create a new image using the recimg command. Entering this command presents a very detailed explanation of how to use it.
You must have administrator privileges to use the recimg command, and you can only access the custom recovery image you create via the Windows 8 refresh feature.
In Windows 10, system recovery has changed. Windows 10 systems don’t come with a recovery partition, which makes it more important than ever to back up your data.
Source: 20 Windows Command Prompt (CMD) Commands You Must Know