Source: 8 Useful Tips & Tricks for SecureCRT – Haifeng’s Blog
All posts by smarc
KeysGen | Find Key Code
Caliper Method
| Root Depth | Key Code |
|---|---|
| 0.329″ | 1 |
| 0.306″ | 2 |
| 0.283″ | 3 |
| 0.260″ | 4 |
| 0.237″ | 5 |
| 0.214″ | 6 |
| 0.191″ | 7 |
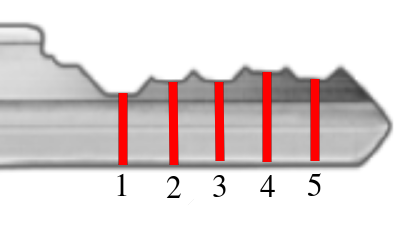
Source: KeysGen | Find Key Code
How to Reuse Decals – Ramp-O-Matic
HOW TO REUSE DECALS
Posted by Ramp-O-Matic Staff on
One of the main hiccups in replacing your pinball machine ramp is finding replacement decals. Most of the time, you can actually reuse your decals! Follow along to see how.
Products I used for this tutorial:
Here we have a Stern Nascar ramp. These Stern decals are actually much thinner than the old Bally/Williams decals, but we can still reuse them!
We will use a can of canned air while inverted to freeze the glue holding the decal on.
Invert the canned air, and spray the liquid all over the decal. Then use a fingernail or knife edge to peel a corner away. You should be able to freely begin dislodging the decal. If it stops peeling, stop pulling and reapply the liquid from the canned air.
Once you have the decal removed, use some goof off, goo gone or other cleaner to remove any remaining adhesive from the decal. Once the decal is clean, we can apply new adhesive.
We will use 3M brand 468MP adhesive sheets to reapply the decal. This material is nothing more than an extremely thin layer of adhesive with no substrate. This material is available on Amazon, and will most often be sold under the “Gizmodorks” label.
Peel some of the backer paper off, and carefully apply the decal to the adhesive.Using a sharp blade, trim the decal away from the rest of the adhesive sheet.
Now you can apply the decal to the finished ramp. Looks like new!
How to Install and Configure Fail2ban on Ubuntu 20.04
Fail2ban Configuration
The default Fail2ban installation comes with two configuration files, /etc/fail2ban/jail.conf and /etc/fail2ban/jail.d/defaults-debian.conf. It is not recommended to modify these files as they may be overwritten when the package is updated.
Fail2ban reads the configuration files in the following order. Each .local file overrides the settings from the .conf file:
/etc/fail2ban/jail.conf/etc/fail2ban/jail.d/*.conf/etc/fail2ban/jail.local/etc/fail2ban/jail.d/*.local
For most users, the easiest way to configure Fail2ban is to copy the jail.conf to jail.local and modify the .local file. More advanced users can build a .local configuration file from scratch. The .local file doesn’t have to include all settings from the corresponding .conf file, only those you want to override.
Create a .local configuration file from the default jail.conf file:
sudo cp /etc/fail2ban/jail.{conf,local}To start configuring the Fail2ban server open, the jail.local file with your text editor :
sudo nano /etc/fail2ban/jail.localThe file includes comments describing what each configuration option does. In this example, we’ll change the basic settings.
Whitelist IP Addresses
IP addresses, IP ranges, or hosts that you want to exclude from banning can be added to the ignoreip directive. Here you should add your local PC IP address and all other machines that you want to whitelist.
Uncomment the line starting with ignoreip and add your IP addresses separated by space:
ignoreip = 127.0.0.1/8 ::1 123.123.123.123 192.168.1.0/24
Ban Settings
The values of bantime, findtime, and maxretry options define the ban time and ban conditions.
bantime is the duration for which the IP is banned. When no suffix is specified, it defaults to seconds. By default, the bantime value is set to 10 minutes. Generally, most users will want to set a longer ban time. Change the value to your liking:
bantime = 1d
To permanently ban the IP use a negative number.
findtime is the duration between the number of failures before a ban is set. For example, if Fail2ban is set to ban an IP after five failures (maxretry, see below), those failures must occur within the findtime duration.
findtime = 10m
maxretry is the number of failures before an IP is banned. The default value is set to five, which should be fine for most users.
maxretry = 5
Email Notifications
Fail2ban can send email alerts when an IP has been banned. To receive emails, you need to have an SMTP installed on your server and change the default action, which only bans the IP to %(action_mw)s, as shown below:
action = %(action_mw)s
%(action_mw)s bans the offending IP and sends an email with a whois report. If you want to include the relevant logs in the email, set the action to %(action_mwl)s.
You can also adjust the sending and receiving email addresses:
destemail = admin@linuxize.com
sender = root@linuxize.com
Fail2ban Jails
Fail2ban uses a concept of jails. A jail describes a service and includes filters and actions. Log entries matching the search pattern are counted, and when a predefined condition is met, the corresponding actions are executed.
Fail2ban ships with a number of jail for different services. You can also create your own jail configurations.
By default, only the ssh jail is enabled. To enable a jail, you need to add enabled = true after the jail title. The following example shows how to enable the proftpd jail:
[proftpd]
enabled = true
port = ftp,ftp-data,ftps,ftps-data
logpath = %(proftpd_log)s
backend = %(proftpd_backend)s
The settings we discussed in the previous section, can be set per jail. Here is an example:
[sshd]
enabled = true
maxretry = 3
findtime = 1d
bantime = 4w
ignoreip = 127.0.0.1/8 23.34.45.56
The filters are located in the /etc/fail2ban/filter.d directory, stored in a file with the same name as the jail. If you have a custom setup and experience with regular expressions, you can fine-tune the filters.
Each time you edit a configuration file, you need to restart the Fail2ban service for changes to take effect:
sudo systemctl restart fail2banFail2ban Client
Fail2ban ships with a command-line tool named fail2ban-client which you can use to interact with the Fail2ban service.
To view all available options, invoke the command with the -h option:
fail2ban-client -hThis tool can be used to ban/unban IP addresses, change settings, restart the service, and more. Here are a few examples:
- Check the jail status:
sudo fail2ban-client status sshd - Unban an IP:
sudo fail2ban-client set sshd unbanip 23.34.45.56 - Ban an IP:
sudo fail2ban-client set sshd banip 23.34.45.56
Source: How to Install and Configure Fail2ban on Ubuntu 20.04 | Linuxize
Getting Started With Hugo: Static Website Generator – LinuxForDevices
The Guitar Fretboard’s Mind-Blowing Mathematics – YouTube
vim – nvim norm command
In neovim 0.4.3-3 in normal mode this command :
:put=range(1,4)
will put numbered list from 1 to 4
but when i want to put numbers only in blank lines like this:
:g/^$/norm :put=range(1,14)
it is not working as expected – only highlighting empty lines but put is not working, why ?
From :help :normal:
{commands}should be a complete command. If{commands}does not finish a command, the last one will be aborted as if<Esc>or<C-C>was typed. A:command must be completed as well.
You can fix that by adding an extra “Enter” character at the end of your command, which you can enter with:
Ctrl+V, Enter
It will display as a ^M in Vim:
:g/^$/norm :put=range(1,14)^M
(There are ways to avoid having to enter a literal “Enter” in your command. For instance, the :execute command is often used for that.)
But in this case there’s a much simpler solution, which is to drop the :normal altogether and just have :g run :put directly!
:g/^$/put=range(1,14)
The :g command will run an Ex command for each line it matches and :put is an Ex command, so you can just cut the middle man here.
Note that what this command does is append 14 new numbered lines after each blank line in your buffer. Not sure if that’s actually what you intended with it or not.
Source: vim – nvim norm command – Unix & Linux Stack Exchange
How to Use Your Bash History in the Linux or macOS Terminal
- Up Arrow or Ctrl+P: Go to the previous command in your history. Press the key multiple times to walk backwards through the commands you’ve used.
- Down Arrow or Ctrl+N: Go to the next command in your history. Press the key multiple times to walk forwards through the commands you’ve used.
- Alt+R: Revert any changes to a command you’ve pulled from your history if you’ve edited it on the current line.
Bash also has a special “recall” mode you can use to search for commands you’ve previously run, rather than scrolling through them one by one.
- Ctrl+R: Recall the last command matching the characters you provide. Press this shortcut and start typing to search your bash history for a command.
- Ctrl+O: Run the command you found with Ctrl+R.
- Ctrl+G: Leave the history searching mode without running a command.
Source: How to Use Your Bash History in the Linux or macOS Terminal
Netplan | Backend-agnostic network configuration in YAML
Create a WordPress admin user with SQL
Create a WordPress admin user with MySQL
If you’ve ever been locked out of a WordPress installation, but have access to the database, here’s a nifty snippet to grant you administrator-level access. There are a couple of things you need to do before using this MySQL code. First, set the variables to your own information. Next, if your WordPress installation is based on a non-standard wp_ table prefix, you must find/replace ‘wp_’ with your current table prefix.
SET@id = 99;SET@user='username';SET@pass ='password';SET@email ='email@ddress';SET@name='Your Name';INSERTINTOwp_users (ID, user_login, user_pass, user_nicename, user_email, user_url, user_registered, user_activation_key, user_status, display_name)VALUES(@id, @user, MD5(@pass), @name, @email,'','2013-06-20 00:00:00','','0', @name);INSERTINTOwp_usermeta (umeta_id, user_id, meta_key, meta_value)VALUES(NULL, @id,'wp_capabilities','a:1:{s:13:"administrator";s:1:"1";}');INSERTINTOwp_usermeta (umeta_id, user_id, meta_key, meta_value)VALUES(NULL, @id,'wp_user_level','10');INSERTINTOwp_usermeta (umeta_id, user_id, meta_key, meta_value)VALUES(NULL, @id,'active','1');
Source: Coderrr | Create a WordPress admin user with MySQL – Coderrr







